The facebook messenger has been leaked and its up for download from Facebook servers.The Messenger has not yet been officially declared but it had been anticipated from a long time.
The messenger basically contains the sidebar as well as the notification system
The best feature is that it can be docked to the right side so it appears as the current facebook sidebar running all along you do other things.
Download for :
Saturday, December 31, 2011
Saturday, December 17, 2011
Get the new google bar
Google is updating it's network with new features.Similar to the new Youtube design the new google bar is another step.
here is a simple hack to activate it:
here is a simple hack to activate it:
- Go to google.com
- In the address bar type:
- Now you will see the new google bar instead of the black bar
Monday, November 21, 2011
View the upcoming new Youtube Design
Hi
Here is a simple way to check out the upcoming Youtube design
All you need is to add a cookie to your session.Here is how:
Here is a simple way to check out the upcoming Youtube design
| The new Youtube Design |
All you need is to add a cookie to your session.Here is how:
- Go to youtube.com
- In the address bar, type :
javascript:document.cookie="VISITOR_INFO1_LIVE=ST1Ti53r4fU"
and press enter - Now open Youtube.com to experience the new look.
Sunday, November 6, 2011
Destroy websites using angry birds
Our favorite angry birds are now destroying websites!!!
This trick works for all the websites. All you need to do is to copy the script below to your browser's address bar and press enter.Wait for some time for the birds to show
This trick works for all the websites. All you need to do is to copy the script below to your browser's address bar and press enter.Wait for some time for the birds to show
Wednesday, October 19, 2011
Hang Computer with a URL
This is an amazing trick.This will hang your computer. All one needs to do is to visit the link below
Note open the link at your own risk
http://tiny.cc/ibJUN
What actually happens is this page floods requests to open mailto windows causing system to hang.
This hack points out inability of modern browsers to block automated "mailto" windows.It should be noted that the modern browsers are however able to block popup windows and alerts.
Note open the link at your own risk
http://tiny.cc/ibJUN
What actually happens is this page floods requests to open mailto windows causing system to hang.
This hack points out inability of modern browsers to block automated "mailto" windows.It should be noted that the modern browsers are however able to block popup windows and alerts.
Sunday, September 18, 2011
HACK Gmail : Social Engineering Method
Hi
Hacking gmail is not an easy task, but social engineering method can make it quite easy. The outline of method is this: we will impersonate as our victim and claim to gmail that my account is hacked,tricking the system to give away the password resetting option and hence allowing us to enter the account of the victim.
For this, we need some information about the victim:
Hacking gmail is not an easy task, but social engineering method can make it quite easy. The outline of method is this: we will impersonate as our victim and claim to gmail that my account is hacked,tricking the system to give away the password resetting option and hence allowing us to enter the account of the victim.
For this, we need some information about the victim:
- creation month and year of account
- Five commonly contacted people.
- Labels used(usually people do not change them so you can try the standard ones if you have no idea about them).
- Other google products used and their approximate months of start.
- any older password (may be able to break in without it, but the more the better)
Sunday, August 14, 2011
Track Sent Emails
Emailing has become very common.While sending important mails we need to be notified whether the person on the receiving end has read the email.Luckily, the tools have been developed.
The Classic
Some email programs(e.g. squirrelmail) use the classical method which requests the user using an alert to send receipt of email.But the receiver always has the upper end. He/She may disable sending the receipt rendering the feature useless.
The Classic
Some email programs(e.g. squirrelmail) use the classical method which requests the user using an alert to send receipt of email.But the receiver always has the upper end. He/She may disable sending the receipt rendering the feature useless.
Sunday, July 31, 2011
Google + Invitations
Google + is a social networking site released by google earlier this year to capture the rapidly increasing social networking market.
Currently, you are not able to join Google + even if you have an invitation.But there is a loohole through which you can invite your friends to join Google +.Here is how:
You can comment here if you need to be added to Google + or directly go to this page.
Currently, you are not able to join Google + even if you have an invitation.But there is a loohole through which you can invite your friends to join Google +.Here is how:
- Ask your friend to add you in a circle.
- An option will appear to add you by email.
- Now enter the name of your friend and click add
- Now a green bar will appear at the bottom of your page with an option saying "Invite [name] to Google +"
- On clicking it a popup will appear asking you to invite your friend.
You can comment here if you need to be added to Google + or directly go to this page.
Tuesday, June 21, 2011
Reverse Image Search by Google
You all must have have heard about tineye.It basically allows you to upload an image and search images of which the image is a part of.The problem with tineye was its small database.
Now google has launched such a service too.It can be accessed at google images. You can either upload image form your computer or search by specifying the image url.
Go to images.google.com
Now google has launched such a service too.It can be accessed at google images. You can either upload image form your computer or search by specifying the image url.
Go to images.google.com
and click on the camera icon .
Wednesday, May 4, 2011
Disposable Email addresses
Disposable email addresses are email address which expire whenever you want.This basically is done to keep the spam away.As you might know that many service providers are providing email alias but most of them can be easily be filtered and hence your email id may be accessible.On the other,disposable email addresses provide you with an entirely different email address and hence saving you from spam.
Some of the service providers are:
Some of the service providers are:
- 33mail.com: Its a free service and provides unlimited disposable addresses,however in the free account you get limited but generous bandwidth.Once you pick up a username,for example disposable,you can create any disposable email address like ex@disposable.33mail.com whenever you want without even informing it to 33mail.These email address will be forwarded to your actual email address that you used for registering.You can cut those email address whenever you want by unsubscribing them through the link provided in each of the forwarded emails.I personally prefer this service.It's fast and free.
Sunday, April 24, 2011
Be Safe From short url's
You must have come across urls like http://goo.gl/XoG1z .They surely make it easier to share and remember long urls but are prone to be used by hackers.Since you so not know what site you are being redirected to beforehand this exploit can easily be used for phishing and other illegitimate uses.
In order to know beforehand the url you are opening it's better to check out to what url you are being redirected.
For url shortened by google(like the one shown before) you can add a '+' symbol to get the info.For example to get info about http://goo.gl/XoG1z just go to http://goo.gl/XoG1z+
For all other url short urls you can visit longurl.org they decode for a number of services.You can also get their firefox addon(it works for firefox4 and firefox 5.it also works for ff6 but somehow it shows incompatible) and Chrome extension.
In order to know beforehand the url you are opening it's better to check out to what url you are being redirected.
For url shortened by google(like the one shown before) you can add a '+' symbol to get the info.For example to get info about http://goo.gl/XoG1z just go to http://goo.gl/XoG1z+
For all other url short urls you can visit longurl.org they decode for a number of services.You can also get their firefox addon(it works for firefox4 and firefox 5.it also works for ff6 but somehow it shows incompatible) and Chrome extension.
Thursday, April 7, 2011
Lock Folders in windows xp and windows 7
Hi all, to lock folders is sometimes a necessity.The process is quite simple
LOCKING
first of all put all the files you want to lock in a folder,let's say "lock".Now rename the folder to
"lock.{2559a1f2-21d7-11d4-bdaf-00c04f60b9f0}" for windows7
"lock.{FEF10DED-355E-4e06-9381-9B24D7F7CC88}"for windows xp
but the folder will still appear to be named as "lock" with added security such as nothing will happen when you try to open it.
LOCKING
first of all put all the files you want to lock in a folder,let's say "lock".Now rename the folder to
"lock.{2559a1f2-21d7-11d4-bdaf-00c04f60b9f0}" for windows7
"lock.{FEF10DED-355E-4e06-9381-9B24D7F7CC88}"for windows xp
but the folder will still appear to be named as "lock" with added security such as nothing will happen when you try to open it.
Sunday, April 3, 2011
Hack Facebook Groups
First things first---not all groups can be hacked.Only groups having an email id can be hacked,typically groups having email id will show their email id on their page (as shown in highlighted part of image) .
You must also know art of fake mailing(Learn here!).
The last thing you need to know is the email address of victim registered with facebook.
Facebook groups have a feature that by enabling email address for group,it's users can post in group using an email.The problem with this feature is that it does nothing to verify identity of user except his/her email address which can easily be faked.
To post in group, simply mail the group such that the mail received by group id looks like:
From: victim@example.com
To: hacked@groups.facebook.com
Sub: wall
Body: Here insert the text you want to post from your victim's email address
The post will appear almost instantly.
Enjoy!!!
You must also know art of fake mailing(Learn here!).
The last thing you need to know is the email address of victim registered with facebook.
Facebook groups have a feature that by enabling email address for group,it's users can post in group using an email.The problem with this feature is that it does nothing to verify identity of user except his/her email address which can easily be faked.
To post in group, simply mail the group such that the mail received by group id looks like:
From: victim@example.com
To: hacked@groups.facebook.com
Sub: wall
Body: Here insert the text you want to post from your victim's email address
The post will appear almost instantly.
Enjoy!!!
Tuesday, March 29, 2011
Backtracking Emails
Most of us believe that the email message sent to them is determined by "FROM" header,but it cannot be denied that most of the times it's forged(Learn How).
The question then arises how to determine where the email came from? You have to understand how email messages are put together in order to backtrack an email message. SMTP is a text based protocol for transferring messages across the internet. A series of headers are placed in front of the data portion of the message. By examining the headers you can usually backtrack a message to the source network, sometimes the source host.
If you are using Outlook or Outlook Express you can view the headers by right clicking on the message and selecting properties or options.If you are using Gmail you need to click on "show original"(click on down arrow next to reply while reading a mail).For Yahoo:In the full message view,"View Full Header" option is placed under the "Actions" tab.
Now Let's Start actual work.Let's Take an example
Monday, March 28, 2011
Spoof Mailing-Send fake email
Spoof mailing is a technique to send email as someone else.It means if my email id is abc@example.com
then sending someone email to appear as if it was sent by me ,in other words,it appears to receiver that he/she has received email from abc@example.com.
There are many free sites available which enable you to send fake emails for free.Some of them are:
and many more....
but the problem is that most of these services do not mail the message instantly.Moreover, most of these can easily be identified.I prefer to send mail from my own script.
It's really easy if you know a little bit of php.But I have shared download link for the script
All you have to do is register and get a free hosting account(say on x10hosting.com) and unzip the file.
Keep both the files in the same folder (or you may upload the folder itself ,if possible).Suppose you got abc.x10hosting.com and uploaded the folder in the main directory then you can access the prank mail sender on abc.x10hosting.com/prank
Please note that you may be violating the terms and conditions you agreed to while signing up.Also some hosting sites do not such scripts to run
DOWNLOAD THE SCRIPT
You may also want to read:Backtracking Emails
then sending someone email to appear as if it was sent by me ,in other words,it appears to receiver that he/she has received email from abc@example.com.
There are many free sites available which enable you to send fake emails for free.Some of them are:
and many more....
but the problem is that most of these services do not mail the message instantly.Moreover, most of these can easily be identified.I prefer to send mail from my own script.
It's really easy if you know a little bit of php.But I have shared download link for the script
All you have to do is register and get a free hosting account(say on x10hosting.com) and unzip the file.
Keep both the files in the same folder (or you may upload the folder itself ,if possible).Suppose you got abc.x10hosting.com and uploaded the folder in the main directory then you can access the prank mail sender on abc.x10hosting.com/prank
Please note that you may be violating the terms and conditions you agreed to while signing up.Also some hosting sites do not such scripts to run
DOWNLOAD THE SCRIPT
You may also want to read:Backtracking Emails
Monday, March 14, 2011
Get Most out of Facebook Feed
Facebook has recently updated it's news feed (using which posts on your home page is shown). The new feed updates and shows posts by your friends with whom you have recently contacted. As a result, if you have not been in touch with a specific friend reently, you might not be able to see his/her wall posts at all.But there is no need to panic,you can still get latest feeds from your all of the friends.Here is what you got to do.
Go to your home and scroll down to the end until it shows the option 'Older Posts'.
Click on 'Edit Options'
Select 'All of your friends and pages' under the 'Show Posts from:' menu.
and done!!!
Go to your home and scroll down to the end until it shows the option 'Older Posts'.
Click on 'Edit Options'
Select 'All of your friends and pages' under the 'Show Posts from:' menu.
and done!!!
Saturday, February 26, 2011
Make Free International Phone Calls Without Disclosing Your Identity
Making phone call can become handy when needing to call a friend.Now that phones have occupied an important part in our daily life making a phone call has become handy.But it becomes really comfortable when making an international call through internet and that too for free.No software or registration is required.All you got to do is to visit
http://www.evaphone.com
Follow the following steps to make the phone call:
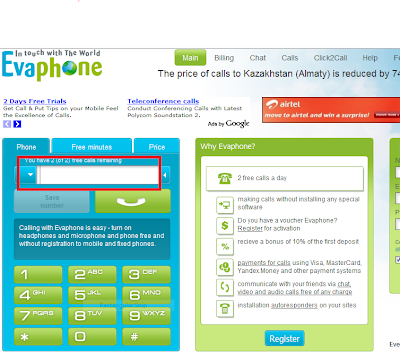
http://www.evaphone.com
Follow the following steps to make the phone call:
- Go to http://evaphone.com
Enter the number(along with the country code) in the marked location and press green button(you might be asked for permissions) and wait for the call to connect....
Enjoy!!!!Friday, February 18, 2011
How To check a Phishing Site??
Phishing is an attempt to hack your web accounts by displaying a similar looking page which redirects you to main website but also stores your password.This is very harmful as the hacker has your password with your knowledge.So it important to check whether the site is a phishing site or not.
To check for a phishing site just copy and paste the following in the address bar of your browser( where you type the address of the site you want to visit):
javascript:alert("The actual URL is:\t\t" + location.protocol + "//" + location.hostname + "/" + "\nThe address URL is:\t\t" + location.href + "\n" + "\nIf the initial part of addresses do not match, this may be a phishing website.");
This code is basically a javascript commands which finds the location of where the site is hosted and the url of page.
To check for a phishing site just copy and paste the following in the address bar of your browser( where you type the address of the site you want to visit):
javascript:alert("The actual URL is:\t\t" + location.protocol + "//" + location.hostname + "/" + "\nThe address URL is:\t\t" + location.href + "\n" + "\nIf the initial part of addresses do not match, this may be a phishing website.");
This code is basically a javascript commands which finds the location of where the site is hosted and the url of page.
Monday, February 14, 2011
Is Your E-mail Account Hacked??
With rise in popularity of internet our dependence on internet has increased and it can be horrifying to find your account controlled by someone else.Here are some measures that you must take in order to recover your account.
Gmail
Yahoo/HotmailGmail
- The first thing to do is to try to reset your password.You can reset your password from here: https://www.google.com/accounts/recovery?continue=https%3A%2F%2Fmail.google.com%2Fmail%2F%3Fui%3Dhtml%26zy%3Dl&hl=en&service=mail&ss=1<mpl=default
- If somehow you get access to your account, the first thing to do is to sign out other sessions if you have logged in anywhere else.To do this you need to first login.At the bottom of page you will notice 'Details'. Click on it, you will notice 'Sign Out All Other Sessions'.This will log you out from any other place where you left your account open.
- If still you cannot access your account,report that your account is hacked,you can report to Gmail here: https://www.google.com/support/accounts/bin/request.py?hl=en&contact_type=acc_reco&ara=2&ctx=acc_reco&rd=1
Unfortunately,yahoo or hotmail do not support any other feature except resetting your password.you can reset you password by reporting.You can reset your password by verifying your identity.You can get the reset link from here:
Yahoo: https://edit.india.yahoo.com/forgotroot?done=http%3A%2F%2Fin.yahoo.com%2F&src=fpctx&partner=&intl=in
Hotmail: https://account.live.com/ResetPassword.aspx
Facebook:
Facebook has inbuilt many safety features.It checks your identity before logging in if someone tries to access your account from a different location(even with the correct password).This feature has made hacking your account by phishing almost impossible.
You can reset your password from here:
https://www.facebook.com/recover.php
Wednesday, February 9, 2011
Email alias by GMail and MSN
Gmail and MSN had been in war for long.This time MSN has gone one step ahead.
Initially gmail provided email alias for gmail users in the following forms
Now MSN taken this fight to next level. MSN already provides the dot feature mentioned above but from now on you get 5 more email alias making it as good as getting a new email account.What it means is that if you own mail@hotmail.com you can get all mails sent to message@hotmail.com if you set it as your email alias.
Also note that other sites such as facebook,twitter,etc treat all email alias as a separate email id so you can register many facebook accounts ,or for that matter on any site, with just one email account!!
Initially gmail provided email alias for gmail users in the following forms
- dot(.) can be used anywhere within the username as another id,for eg. if you own mail@gmail.com then you also own m.ail@gmail.com, ma.il@gmail.com,etc.
- you can use addition symbol(+) after username to get your mails ,i.e. if you own mail@gmail.com then all mails sent to mail+new@gmail.com will also be sent to you.
- you are also allowed capitalization of some or all the alphabets in your username ,for eg. if you own mail@gmail.com then you also own MaIl@gmail.com ,MAIL@gmail.com,etc.
Now MSN taken this fight to next level. MSN already provides the dot feature mentioned above but from now on you get 5 more email alias making it as good as getting a new email account.What it means is that if you own mail@hotmail.com you can get all mails sent to message@hotmail.com if you set it as your email alias.
Also note that other sites such as facebook,twitter,etc treat all email alias as a separate email id so you can register many facebook accounts ,or for that matter on any site, with just one email account!!
Tuesday, February 8, 2011
How to Delete Your Facebook Account
If you have tried to delete your Facebook account you may find it almost impossible to do so.
You may find the link to deactivate your account(which is not the same as deleting your account ).When you deactivate your account it will appear to other people that you no longer exist on facebook.But as soon as you log in again you will find all your data intact.It is almost same as not logging in for a long time.If you want to deactivate your account, here is the link
www.facebook.com/deactivate.php
Actually facebook has hidden the delete account link within its help center.It is very difficult to look for.If you want to delete your account, here's the link
You must keep in mind that once you hve deleted your account you can never get the associated data back
Thursday, January 27, 2011
Security Holes In Facebook
Do you know anyone can update your facebook status!!!!
Anyone can upload worms on facebook!!!!
Not just you,even your friends are not safe!!!
Yes,it's true.
Following are some security holes in facebook:
1. Profile Access
If you have activated facebook mobile your account is at danger.The thing is, when updating status or any such command via phone,facebook does not ask for your password.So all one have to do is send a message to facebook such that it appears that it is sent from your number.The trick is called Spoof messaging.There are a lot of sites providing this service.One such site is http://www.smsglobal.com/ .They provide 25 free messages.
Using this hole anyone can
How to be safe: Do not activate Facebook Mobile.
2. Accessing Deleted Images
If you think that once you delete an photo it will not be visible to others,then you are wrong.
Once you delete an image only it's link is deleted,not the image...So if you have thelink you can still access a deleted image.So be careful with what you upload!!
3.Facebook is vulnerable to Worms
Facebook can be infected with worms by creating an application.Recent Rotating images worm proves it.It posted status messages automatically, looking something like this:
Hi Friends see Face-book images rotate 360* see here >> http://SHADYCLOUDS.TK/
Really cool Facebook revolving images. MUST SEE http://rotatingimage2.tk/ .
Some are calling it as “social XSS” attack,i.e. any script from friend tempts you to run the same script from address bar.And any such script as if it was hosted on facebook.com and can do everything which the logged-in user can do (unless facebook detects and catches malicious automated action).
How to be safe: Do not allow access to any application unless you completely trust it.
Note: I do not intend to cause damage to social image of facebook in any form.This tutorial is for educational purposes only.I am not responsible for misuse of information posted in any form.
Anyone can upload worms on facebook!!!!
Not just you,even your friends are not safe!!!
Yes,it's true.
Following are some security holes in facebook:
1. Profile Access
If you have activated facebook mobile your account is at danger.The thing is, when updating status or any such command via phone,facebook does not ask for your password.So all one have to do is send a message to facebook such that it appears that it is sent from your number.The trick is called Spoof messaging.There are a lot of sites providing this service.One such site is http://www.smsglobal.com/ .They provide 25 free messages.
Using this hole anyone can
- Update your status
- Message
- Get Profile Information of your friends
- Get cell phone number of your friends
- Wall post
- Poke
- Add your friend
- Write a note
- Comment on your status
How to be safe: Do not activate Facebook Mobile.
2. Accessing Deleted Images
If you think that once you delete an photo it will not be visible to others,then you are wrong.
Once you delete an image only it's link is deleted,not the image...So if you have thelink you can still access a deleted image.So be careful with what you upload!!
3.Facebook is vulnerable to Worms
Facebook can be infected with worms by creating an application.Recent Rotating images worm proves it.It posted status messages automatically, looking something like this:
Hi Friends see Face-book images rotate 360* see here >> http://SHADYCLOUDS.TK/
Really cool Facebook revolving images. MUST SEE http://rotatingimage2.tk/ .
Some are calling it as “social XSS” attack,i.e. any script from friend tempts you to run the same script from address bar.And any such script as if it was hosted on facebook.com and can do everything which the logged-in user can do (unless facebook detects and catches malicious automated action).
How to be safe: Do not allow access to any application unless you completely trust it.
Note: I do not intend to cause damage to social image of facebook in any form.This tutorial is for educational purposes only.I am not responsible for misuse of information posted in any form.
Monday, January 24, 2011
SQL Injection
Usually sites ask you to login before you can view specific information.But you can bypass it without even knowing the username or the password.The trick is SQL Injection .
Suppose you fill in the login screen like this:
User:abc
Password:pqrs
Now the script will make an enquiry to the server like this:
SELECT USER from database WHERE username=’abc’ AND password="pqrs"
Now this can be exploited in a number of ways:
username:’ or 1=’1 password:’ or 1=’1
username:’ or ’1′=’1′ password:’ or ’1′=’1′
username:or 1=1 password:or 1=1
username:'1=1-' password: [Note:after '-' remaining line is treated as comment]
There are a lot of ways out there....
Note:This post is for educational purposes only.I am not responsible for its misuse in any way.
Suppose you fill in the login screen like this:
User:abc
Password:pqrs
Now the script will make an enquiry to the server like this:
SELECT USER from database WHERE username=’abc’ AND password="pqrs"
Now this can be exploited in a number of ways:
username:’ or 1=’1 password:’ or 1=’1
username:’ or ’1′=’1′ password:’ or ’1′=’1′
username:or 1=1 password:or 1=1
username:'1=1-' password:
There are a lot of ways out there....
Note:This post is for educational purposes only.I am not responsible for its misuse in any way.
Saturday, January 8, 2011
Some Important definitions and Information
ISO:
A file that is created from an image of a CD. You can make an iso yourself with a program such as Adaptec Easy CD Creator, or you can burn an ISO file to a CD-R to create a copy of a CD.
Lomography 35mm 36 Exposure 400 ISO film - 3 pack
Bin/cue files:
These are also used to create an image of a CD. Most people burn these with CdrWin or Fireburner. The .bin file contains all the data for the cd, the .cue file is just a small file in text format telling the software exactly how to burn the data onto the CD.
Sterling Replacement Cue Ball
MP3:
Don't know what these are? What cave have you been you living in? This is a format used to compress music files. You can create your own by encoding .wav files ripped from audio CDs. There are many free players that will play mp3s for you (see the Winamp tutorial)
Coby 4 GB Video MP3 Player with FM Radio (Red)
Ace files:
These are used to compress/archive data. Use WinAce to decompress them, or to make your own. The normal format for ace files is to have .ace, .c01, .c01, etc.
Dsi Media Kit - Black
Rar files:
Another compression/archive format. This is most commonly used on iso or bin files in order to split them up into smaller files (15 MB is the norm). Winrar and many other utilities can decompress these. Rar files are usually in the format .rar, .r01, .r02, etc. But don't be surprised if you don't see a .rar file. Just open up winrar and point it to .r01. You also may see them packed as .001, .002, etc. (maybe with a .rar, maybe not)
WinRAR 3.93, x32 bit, Archiver & Compression software for MS Windows OS, 1-User Key
Pub:
This is an FTP that has left on anonymous access. Many are owned by large companies, so they have a lot of bandwidth. This makes it possible for one person to send files there and many people can download them at once =) These are found by scanning ranges of ips . Just remember, like the name says, these are public. Just because you upload something there or make directories with your name does not make it 'your pub'. At the same time, realize that if you come across a pub with another person/groups stuff on it that it may be in use to build other pubs from - so don't ruin it for many people by deleting stuff you find there. For more on this, go read some posts on our Bulletin Board.
Proxy:
A system that is set up to forward packets... There are many different kinds, check out the proxy tutorial for more info. Basically, a proxy server helps cover up your tracks because you connect to remote computers through the proxy. Think of it as the condom of the Internet
SFV Files/ CRC Checks:
SFV files contain information about files that they accompany. You can preform a CRC check on the files using a program such as WinSFV. This compares the information in the SFV file to the file itself. If the information doesn't match, then the file was probably messed up in transfer somehow.. try downloading it again, from a different source if possible.
0-Day:
Latest software releases.
0-Sec:
Same as above, although the period of time between ripping a game or application and it appearing on a warez site is even shorter.
Ace File:
The first file in a series of compressed archives (the one you double click on to decompress all the files at once).
Active List:
Similar to a mailing list, but uses ICQ to send instant messages to subscribers.
Alpha:
Software receives this label when it is in the very early stages of development. Usually full of bugs, so don't touch it with a barge pole.
Anti-Leech:
A system which uses cgi scripts to prevent people stealing links and then taking the credit for uploading the files.
Appz:
Short for applications. For example Flash 5 or GoLie 5.5.
ASF File:
The worst quality movie file format (still pretty good though), much smaller in size than dat or mpg.
Banner Site:
Password and username restricted FTP site. To get the correct login details you must click on several banners.
Beta:
An acronym for Business Software Alliance, an organisation who are responsible for enforcing anti-piracy litigation. Similar groups in charge of controlling software "theft" include the SIIA, SPA and ELSPA.
BSOD:
Many people read about BSODs on bulletin boards and think that they're being insulted, but there is no need to get paranoid. It is actually an acronym for "Blue Screen Of Death". These can occur for a multitude of reasons (old Bill likes to keep us guessing!) and are the bane of PC user's lives.
Bulletin Board:
A virtual meeting place on the web similar to a chat room except that it isn't in real time. One person leaves a message then others come along, read it and add a reply. Each new discussion is called a new topic or thread and has it's own link. Whenever a new topic is created the older topics are pushed one place downwards in the list. When someone replies to an older topic it is brought back to the top of the list.
C?? File:
File extension that indicates that a file is part of an .ace or .rar series of compressed files.
Cgi Scripts:
These are referrers which are used in url’s. When you click on a link with a ?cgi reference you are directed to a sponsor’s website or an anti-leech protected file.
Cookie:
A tiny text file (usually less than 1kb), which is stored on your hard drive when you visit a web site. These are used to remember who you are so that you can access members only areas on the site without having to type in a password every time or to retain your personalised settings so that they are available the next time you visit.
Courier:
Someone who is involved in the logistics of delivering new releases directly from the release groups themselves to FTP sites.
Crack:
A tiny executable file that is used to transform a shareware program into the full version. Also used to remove any copy protection from the main executable of games (this will already have been done in "ripped" warez games).
CRC Error:
These can occur when you try to decompress a file that has become corrupt during the downloading process, usually as a result of too much resuming.
Credits:
The amount of data you are permitted to download from a ratio site. The more credits you have the more software you are allowed to download.
DAP:
A quick way of referring to "Download Accelerator Plus", a free download manager that claims to speed up file transfers by up to three hundred per cent. It works by making multiple connections to the same file and is paid for by revolving advertising banners.Also supports resume. **EDITOR'S PICK**
DAT File:
File format used for movies, identical in quality and size to mpg as far as I can tell.
DC:
The lazy way of referring to the Dreamcast, Sega's latest console incarnation.
Decompression:
Unpacking many files that have been stored in a single archive.
Distro:
A concise means of referring to a distribution FTP site. These are huge storage areas which act as a springboard for the transfer of new releases. Their whereabouts are never public disclosed to aid their survival rate. You can think of them as the initial source from which warez emanates.
Direct Downloads
Links to actual files rather than other warez sites or pages. These are usually gathered together from many different sites and put on one page for your convenience.
DivX:
Movies ripped from a DVD using the DivX video codecs. Can be played back using Media Player.
DIZ File:
Short for description. Very brief text file found in warez archives stating the title of the software, the number of files that makes up the set and the group who released it.
Download (or DL):
Copying files from a web server or FTP site to your computer using a modem.
Emulator:
An application that simulates another computer system or console using your PC.
FAQ:
Stands for Frequently Asked Questions.
FAW:
Abbreviation for "Files Anywhere", a popular, free web storage service.
File Transfer Protocol (FTP):
The method used to transfer files from one computer to another using a modem.
Flaming:
A general net term for "verbally" attacking someone. This can be done via email, bulletin board, chat room or any medium which involves communication across the web.
Freedrive:
Virtual hard drive storage area on the web. Free to join and anything and everything can be uploaded or downloaded.
Freeware:
Unrestricted software that is downloaded from the net and is completely free to use. Often paid for using advertising.
FTP Client / Browser:
A program used to access, upload and download data from FTP sites.
Fxp:
The art of transferring data from one Ftp site to another using the connection speed of the slower of the two computers.
Gamez:
Pretty self-explanatory this one.
Getright:
One of the best download managers available.
Gold:
A piece of software is said to have gone gold when the final version is complete and it is ready to ship to the public.
Gozilla:
Another excellent download manager.
Hacking:
Gaining access to a remote computer without the authorisation to do so. Usually for the purposes of stealing confidential information or the malicious destruction of data.
Hammering:
Repeatedly trying to access an FTP site using an FTP client or download manager.
HTTP:
Stands for "Hypertext Transfer Protocol". The method you use to view a web page. Always comes before the address of a website in your Url bar.
ICQ:
Derives from the term "I Seek You" and is used for real time chat and transferring files over the internet.
IP Address:
A series of numbers separated by dots used to identify your computer on the Internet.
IRC:
Stands for "Instant Relay Chat". Used for real time chat and transferring files over the Internet.
ISO:
An exact copy of an original CD, all the multimedia bits and pieces are uncut and therefore they are extremely large and awkward to download.
Java:
Html scripts used to add functionality to or bring web pages alive. These include animation (such as the title graphic on my main page), menus, chat rooms, buttons, pop ups and so on.
Key Generator:
A tiny executable program that is capable of creating a serial number from a specified username. These are specific to particular applications or utilities, so a serial number created with one key generator will only work for the program for which the key generator was developed.
Lamer:
An annoying and overused general derogatory term used to insult/put down anyone and everything.
Leeching:
Downloading files without giving anything back in return or copying other people’s links.
Mirror:
An exact copy of a web site that is stored on a different server. Using multiple locations for warez sites allows the site to be accessed using a different address if the main site is deleted.
Modchip:
Very common website sponsor found on warez sites. They don’t mind their banners being used on illegal software sites because their products are one of the “grey areas” of the law. Modchips are small pieces of electronic circuitry which allow copied games to be played on your Playstation. If a Playstation has been fitted with a Modchip it is said to have been "chipped".
MP3 File:
Compressed music file format. Average track size is between 3 and 4 meg compared to 40-ish meg in wav format.
MPG File:
The best quality and largest movie file format.
Multi Web Space Faker:
A tool used to create lots of free web space accounts simultaneously.
Name Zero:
An organisation that offers free website domain names. The main drawbacks are that you have to put up with a very bulky banner residing at the bottom of your page and the fact that you never actually own your chosen address.
NFO File:
Short for info or information. Basic text file containing all the important details relating to a particular release, such as number of files, release date, copy protection system, installation instructions etc.
Nuked:
A release is said to be nuked if it is completely unplayable. Usually when this happens another group re-releases the particular game, although fixes do sometimes follow on to rescue the game from trash can.
OEM:
An acronym for Original Equipment Manufacturer. OEM software products are repackaged versions of the full retail product. They are often re-branded to suit the needs of the particular vender and are much more reasonable priced because they lack excessive packaging and a hard copy of the manual.
OST:
Not strictly a warez term this one, but one that you are likely to come across while searching for MP3 music. It stands for original soundtrack (movie music).
Patch:
We all know games and applications aren't perfect. When they are released we would hope that they have been thoroughly tested for bugs and incompatibility problems, but you can guarantee that many of these will still slip through the quality control net. Once the program is released to the general public, the bug reports start to flood in. A patch is a downloadable executive file which takes these reports into account and attempts to incorporate all the fixes for these known problems. A patch can resolve incompatibility problems, prevent crashes or improve the performance of a piece of software.
Piracy:
The replication and distribution of videos or computer software.
Pop-ups:
Irritating browser windows that open automatically when you visit a warez site. Usually contain voting portals or porn sites.
Port:
A port is a term used when referring to FTP sites and is an essential extension of the address used to access them. If the port number of an FTP site isn't specified the default setting of 21 will automatically be used.
Pron:
A long time ago in a galaxy far, far away someone posted a request for porn on a bulletin board, only, because of a typing error what he ended up asking for was "pron". Since then this has become a bit of a running joke and so it is now deliberately misspelled.
Proxy:
A third party server which acts as an anonymous go between whenever you request a web page or contact a remote server. The message from your computer is first sent through the proxy server before being relayed to the final destination so that it appears as though the request has come from the IP address of the proxy server rather than you. Used when you wish to maintain your privacy on the net or speed up your connection (much more detailed info on this subject in the "more tips" section).
Psx:
A quick way of referring to the Sony Playstation.
Pub:
A free for all FTP site where anonymous access is permitted.
Pub Scanner:
Someone who scours the net for anonymous access FTP sites which permit the creation and deletion of files. These are then exploited by uploading software for others to share.
Pub Stealer:
Someone who posts the IP address of a public FTP site which they themselves have not built. Some pub stealers justify this by claiming that the elitism of private FXP groups discriminates against those people who do not have access, yet others simply post other people's work to try to claim the credit for themselves. Either way though, pub stealers are despised by the FXP groups and praised by those who would otherwise not have access to them.
Rar File:
The first file in a series of compressed archives (the one you double click on to decompress all the files at once). Usually decompressed using a program called Winrar.
Release Groups:
A group of people who are involved in cracking and / or ripping software and then repackaging it into easily downloadable segments.
Ratio:
Two numbers separated by a semi-colon. Indicates how much data you must upload to an FTP site before you are permitted to download anything.
Reg File:
Tiny file that adds essential configuration details into the registry.
Resume:
The ability to stop and start downloading / uploading a file whenever you choose without having to start from the beginning again.
Rip:
Software that has had all the non-essential gubbins removed to reduce its size. Videos and music are always the first casualties.
Raped:
A release is branded with this term if it has been damaged beyond repair during the ripping process.
RM File:
Shorthand for Real Media, a file format used to encode video sequences, which can only be played back using the "Real Player". Video clips produced using this format are not of the highest quality, but do have the advantage of a small file size.
ROM:
Games which are designed for other platforms, but are played on the PC using an emulator.
Serial:
A valid username and password that is saved as a basic text file and is used to register a shareware program and therefore remove all the restrictions.
Shareware:
Try before you buy software downloaded from the net.
Spam:
Unsolicited junk e-mail. Supposedly stands for "Stupid Person's Annoying Message".
Sponsor:
To make some money webmasters can place adverts on their sites. Each time you click on these adverts or banners they get paid a few cents for bringing potential customers to the sponsors website.
Surfer Friendly (SF):
Surfer friendly sites supposedly have no blind links, pop-ups or porn banners. Don't be fooled by this label though as some sites will tell you fibs to get you to visit them.
Sys Op:
The person who has the responsibility for running the computer from which an FTP site has been established. When warez is uploaded to public FTP sites and then suddenly goes "Missing In Action" you can often lay the blame at the door of the Sys Op who has an obligation to make sure his/her server stays within the boundaries of the law (i.e. warez free).
Top List:
Chart which lists in rank order the best warez sites. Worked out on the basis of votes.
Trading:
Swapping warez, file for file via FTP, ICQ etc. Not usually approved of by the real warez community who believe that warez should be freely distributed. To put it simply, it is not the "warez way".
Trainer:
A small, executable program which sits in your taskbar while you play a game. Hotkeys are associated with cheat commands so that when they are pressed you are given extra ammo, weapons, lives or the ability to toggle between invincible/mortal modes etc etc.
Trojans:
Nasty virus like attachments which can be merged with executable files. These are tiny so are unlikely to arouse suspicion. When run they allow a hacker to access your computer and wreak havoc. Can occasionally be found in warez files.
UBB:
Shorthand for Ultimate Bulletin Board, currently the most popular script used for creating warez bulletin boards.
UBB Hacks:
This term falsely gives the impression that something destructive or malicious is involved, but when you hear people talking about a hack in the context of bulletin boards they are simply referring to code which helps to improve the functionality of a board. For example a "thread hack" would effect the way in which individual threads look and operate.
Undeletable Pub:
An anonymous access, public FTP site where the permission attributes are set to allow uploads and downloads, but do not permit deletion.
Unzip:
Unpacking or decompressing many files that have been stored in a single archive. Technically only used when talking about zip files.
Upload:
Copying files from your computer to a web server or FTP site using a modem.
URL:
Stands for "Uniform Resource Locator". The web site address you type into your browser.
Voting:
Members of the warez scene are very keen to reach the number one slot of top lists such as Voodoo, Top 60 etc. and will therefore encourage you to vote for their site to improve their position and get the credit they deserve (or not as the case may be!).
Warez:
Full version software that is uploaded to the internet and is available for free download.
Warez Board:
Bulletin board used by the warez community to share links and discuss anything related to warez.
Winace:
Another utility used for decompressing all the common archive formats. Not great in my opinion. See below for a better one.
Winrar:
Utility used for decompressing .rar files and much more.
Winzip:
An essential tool used to decompress warez files.
Zip:
A common compression format used to store warez .
A file that is created from an image of a CD. You can make an iso yourself with a program such as Adaptec Easy CD Creator, or you can burn an ISO file to a CD-R to create a copy of a CD.
Lomography 35mm 36 Exposure 400 ISO film - 3 pack
Bin/cue files:
These are also used to create an image of a CD. Most people burn these with CdrWin or Fireburner. The .bin file contains all the data for the cd, the .cue file is just a small file in text format telling the software exactly how to burn the data onto the CD.
Sterling Replacement Cue Ball
MP3:
Don't know what these are? What cave have you been you living in? This is a format used to compress music files. You can create your own by encoding .wav files ripped from audio CDs. There are many free players that will play mp3s for you (see the Winamp tutorial)
Coby 4 GB Video MP3 Player with FM Radio (Red)
Ace files:
These are used to compress/archive data. Use WinAce to decompress them, or to make your own. The normal format for ace files is to have .ace, .c01, .c01, etc.
Dsi Media Kit - Black
Rar files:
Another compression/archive format. This is most commonly used on iso or bin files in order to split them up into smaller files (15 MB is the norm). Winrar and many other utilities can decompress these. Rar files are usually in the format .rar, .r01, .r02, etc. But don't be surprised if you don't see a .rar file. Just open up winrar and point it to .r01. You also may see them packed as .001, .002, etc. (maybe with a .rar, maybe not)
WinRAR 3.93, x32 bit, Archiver & Compression software for MS Windows OS, 1-User Key
Pub:
This is an FTP that has left on anonymous access. Many are owned by large companies, so they have a lot of bandwidth. This makes it possible for one person to send files there and many people can download them at once =) These are found by scanning ranges of ips . Just remember, like the name says, these are public. Just because you upload something there or make directories with your name does not make it 'your pub'. At the same time, realize that if you come across a pub with another person/groups stuff on it that it may be in use to build other pubs from - so don't ruin it for many people by deleting stuff you find there. For more on this, go read some posts on our Bulletin Board.
Proxy:
A system that is set up to forward packets... There are many different kinds, check out the proxy tutorial for more info. Basically, a proxy server helps cover up your tracks because you connect to remote computers through the proxy. Think of it as the condom of the Internet
SFV Files/ CRC Checks:
SFV files contain information about files that they accompany. You can preform a CRC check on the files using a program such as WinSFV. This compares the information in the SFV file to the file itself. If the information doesn't match, then the file was probably messed up in transfer somehow.. try downloading it again, from a different source if possible.
0-Day:
Latest software releases.
0-Sec:
Same as above, although the period of time between ripping a game or application and it appearing on a warez site is even shorter.
Ace File:
The first file in a series of compressed archives (the one you double click on to decompress all the files at once).
Active List:
Similar to a mailing list, but uses ICQ to send instant messages to subscribers.
Alpha:
Software receives this label when it is in the very early stages of development. Usually full of bugs, so don't touch it with a barge pole.
Anti-Leech:
A system which uses cgi scripts to prevent people stealing links and then taking the credit for uploading the files.
Appz:
Short for applications. For example Flash 5 or GoLie 5.5.
ASF File:
The worst quality movie file format (still pretty good though), much smaller in size than dat or mpg.
Banner Site:
Password and username restricted FTP site. To get the correct login details you must click on several banners.
Beta:
An acronym for Business Software Alliance, an organisation who are responsible for enforcing anti-piracy litigation. Similar groups in charge of controlling software "theft" include the SIIA, SPA and ELSPA.
BSOD:
Many people read about BSODs on bulletin boards and think that they're being insulted, but there is no need to get paranoid. It is actually an acronym for "Blue Screen Of Death". These can occur for a multitude of reasons (old Bill likes to keep us guessing!) and are the bane of PC user's lives.
Bulletin Board:
A virtual meeting place on the web similar to a chat room except that it isn't in real time. One person leaves a message then others come along, read it and add a reply. Each new discussion is called a new topic or thread and has it's own link. Whenever a new topic is created the older topics are pushed one place downwards in the list. When someone replies to an older topic it is brought back to the top of the list.
C?? File:
File extension that indicates that a file is part of an .ace or .rar series of compressed files.
Cgi Scripts:
These are referrers which are used in url’s. When you click on a link with a ?cgi reference you are directed to a sponsor’s website or an anti-leech protected file.
Cookie:
A tiny text file (usually less than 1kb), which is stored on your hard drive when you visit a web site. These are used to remember who you are so that you can access members only areas on the site without having to type in a password every time or to retain your personalised settings so that they are available the next time you visit.
Courier:
Someone who is involved in the logistics of delivering new releases directly from the release groups themselves to FTP sites.
Crack:
A tiny executable file that is used to transform a shareware program into the full version. Also used to remove any copy protection from the main executable of games (this will already have been done in "ripped" warez games).
CRC Error:
These can occur when you try to decompress a file that has become corrupt during the downloading process, usually as a result of too much resuming.
Credits:
The amount of data you are permitted to download from a ratio site. The more credits you have the more software you are allowed to download.
DAP:
A quick way of referring to "Download Accelerator Plus", a free download manager that claims to speed up file transfers by up to three hundred per cent. It works by making multiple connections to the same file and is paid for by revolving advertising banners.Also supports resume. **EDITOR'S PICK**
DAT File:
File format used for movies, identical in quality and size to mpg as far as I can tell.
DC:
The lazy way of referring to the Dreamcast, Sega's latest console incarnation.
Decompression:
Unpacking many files that have been stored in a single archive.
Distro:
A concise means of referring to a distribution FTP site. These are huge storage areas which act as a springboard for the transfer of new releases. Their whereabouts are never public disclosed to aid their survival rate. You can think of them as the initial source from which warez emanates.
Direct Downloads
Links to actual files rather than other warez sites or pages. These are usually gathered together from many different sites and put on one page for your convenience.
DivX:
Movies ripped from a DVD using the DivX video codecs. Can be played back using Media Player.
DIZ File:
Short for description. Very brief text file found in warez archives stating the title of the software, the number of files that makes up the set and the group who released it.
Download (or DL):
Copying files from a web server or FTP site to your computer using a modem.
Emulator:
An application that simulates another computer system or console using your PC.
FAQ:
Stands for Frequently Asked Questions.
FAW:
Abbreviation for "Files Anywhere", a popular, free web storage service.
File Transfer Protocol (FTP):
The method used to transfer files from one computer to another using a modem.
Flaming:
A general net term for "verbally" attacking someone. This can be done via email, bulletin board, chat room or any medium which involves communication across the web.
Freedrive:
Virtual hard drive storage area on the web. Free to join and anything and everything can be uploaded or downloaded.
Freeware:
Unrestricted software that is downloaded from the net and is completely free to use. Often paid for using advertising.
FTP Client / Browser:
A program used to access, upload and download data from FTP sites.
Fxp:
The art of transferring data from one Ftp site to another using the connection speed of the slower of the two computers.
Gamez:
Pretty self-explanatory this one.
Getright:
One of the best download managers available.
Gold:
A piece of software is said to have gone gold when the final version is complete and it is ready to ship to the public.
Gozilla:
Another excellent download manager.
Hacking:
Gaining access to a remote computer without the authorisation to do so. Usually for the purposes of stealing confidential information or the malicious destruction of data.
Hammering:
Repeatedly trying to access an FTP site using an FTP client or download manager.
HTTP:
Stands for "Hypertext Transfer Protocol". The method you use to view a web page. Always comes before the address of a website in your Url bar.
ICQ:
Derives from the term "I Seek You" and is used for real time chat and transferring files over the internet.
IP Address:
A series of numbers separated by dots used to identify your computer on the Internet.
IRC:
Stands for "Instant Relay Chat". Used for real time chat and transferring files over the Internet.
ISO:
An exact copy of an original CD, all the multimedia bits and pieces are uncut and therefore they are extremely large and awkward to download.
Java:
Html scripts used to add functionality to or bring web pages alive. These include animation (such as the title graphic on my main page), menus, chat rooms, buttons, pop ups and so on.
Key Generator:
A tiny executable program that is capable of creating a serial number from a specified username. These are specific to particular applications or utilities, so a serial number created with one key generator will only work for the program for which the key generator was developed.
Lamer:
An annoying and overused general derogatory term used to insult/put down anyone and everything.
Leeching:
Downloading files without giving anything back in return or copying other people’s links.
Mirror:
An exact copy of a web site that is stored on a different server. Using multiple locations for warez sites allows the site to be accessed using a different address if the main site is deleted.
Modchip:
Very common website sponsor found on warez sites. They don’t mind their banners being used on illegal software sites because their products are one of the “grey areas” of the law. Modchips are small pieces of electronic circuitry which allow copied games to be played on your Playstation. If a Playstation has been fitted with a Modchip it is said to have been "chipped".
MP3 File:
Compressed music file format. Average track size is between 3 and 4 meg compared to 40-ish meg in wav format.
MPG File:
The best quality and largest movie file format.
Multi Web Space Faker:
A tool used to create lots of free web space accounts simultaneously.
Name Zero:
An organisation that offers free website domain names. The main drawbacks are that you have to put up with a very bulky banner residing at the bottom of your page and the fact that you never actually own your chosen address.
NFO File:
Short for info or information. Basic text file containing all the important details relating to a particular release, such as number of files, release date, copy protection system, installation instructions etc.
Nuked:
A release is said to be nuked if it is completely unplayable. Usually when this happens another group re-releases the particular game, although fixes do sometimes follow on to rescue the game from trash can.
OEM:
An acronym for Original Equipment Manufacturer. OEM software products are repackaged versions of the full retail product. They are often re-branded to suit the needs of the particular vender and are much more reasonable priced because they lack excessive packaging and a hard copy of the manual.
OST:
Not strictly a warez term this one, but one that you are likely to come across while searching for MP3 music. It stands for original soundtrack (movie music).
Patch:
We all know games and applications aren't perfect. When they are released we would hope that they have been thoroughly tested for bugs and incompatibility problems, but you can guarantee that many of these will still slip through the quality control net. Once the program is released to the general public, the bug reports start to flood in. A patch is a downloadable executive file which takes these reports into account and attempts to incorporate all the fixes for these known problems. A patch can resolve incompatibility problems, prevent crashes or improve the performance of a piece of software.
Piracy:
The replication and distribution of videos or computer software.
Pop-ups:
Irritating browser windows that open automatically when you visit a warez site. Usually contain voting portals or porn sites.
Port:
A port is a term used when referring to FTP sites and is an essential extension of the address used to access them. If the port number of an FTP site isn't specified the default setting of 21 will automatically be used.
Pron:
A long time ago in a galaxy far, far away someone posted a request for porn on a bulletin board, only, because of a typing error what he ended up asking for was "pron". Since then this has become a bit of a running joke and so it is now deliberately misspelled.
Proxy:
A third party server which acts as an anonymous go between whenever you request a web page or contact a remote server. The message from your computer is first sent through the proxy server before being relayed to the final destination so that it appears as though the request has come from the IP address of the proxy server rather than you. Used when you wish to maintain your privacy on the net or speed up your connection (much more detailed info on this subject in the "more tips" section).
Psx:
A quick way of referring to the Sony Playstation.
Pub:
A free for all FTP site where anonymous access is permitted.
Pub Scanner:
Someone who scours the net for anonymous access FTP sites which permit the creation and deletion of files. These are then exploited by uploading software for others to share.
Pub Stealer:
Someone who posts the IP address of a public FTP site which they themselves have not built. Some pub stealers justify this by claiming that the elitism of private FXP groups discriminates against those people who do not have access, yet others simply post other people's work to try to claim the credit for themselves. Either way though, pub stealers are despised by the FXP groups and praised by those who would otherwise not have access to them.
Rar File:
The first file in a series of compressed archives (the one you double click on to decompress all the files at once). Usually decompressed using a program called Winrar.
Release Groups:
A group of people who are involved in cracking and / or ripping software and then repackaging it into easily downloadable segments.
Ratio:
Two numbers separated by a semi-colon. Indicates how much data you must upload to an FTP site before you are permitted to download anything.
Reg File:
Tiny file that adds essential configuration details into the registry.
Resume:
The ability to stop and start downloading / uploading a file whenever you choose without having to start from the beginning again.
Rip:
Software that has had all the non-essential gubbins removed to reduce its size. Videos and music are always the first casualties.
Raped:
A release is branded with this term if it has been damaged beyond repair during the ripping process.
RM File:
Shorthand for Real Media, a file format used to encode video sequences, which can only be played back using the "Real Player". Video clips produced using this format are not of the highest quality, but do have the advantage of a small file size.
ROM:
Games which are designed for other platforms, but are played on the PC using an emulator.
Serial:
A valid username and password that is saved as a basic text file and is used to register a shareware program and therefore remove all the restrictions.
Shareware:
Try before you buy software downloaded from the net.
Spam:
Unsolicited junk e-mail. Supposedly stands for "Stupid Person's Annoying Message".
Sponsor:
To make some money webmasters can place adverts on their sites. Each time you click on these adverts or banners they get paid a few cents for bringing potential customers to the sponsors website.
Surfer Friendly (SF):
Surfer friendly sites supposedly have no blind links, pop-ups or porn banners. Don't be fooled by this label though as some sites will tell you fibs to get you to visit them.
Sys Op:
The person who has the responsibility for running the computer from which an FTP site has been established. When warez is uploaded to public FTP sites and then suddenly goes "Missing In Action" you can often lay the blame at the door of the Sys Op who has an obligation to make sure his/her server stays within the boundaries of the law (i.e. warez free).
Top List:
Chart which lists in rank order the best warez sites. Worked out on the basis of votes.
Trading:
Swapping warez, file for file via FTP, ICQ etc. Not usually approved of by the real warez community who believe that warez should be freely distributed. To put it simply, it is not the "warez way".
Trainer:
A small, executable program which sits in your taskbar while you play a game. Hotkeys are associated with cheat commands so that when they are pressed you are given extra ammo, weapons, lives or the ability to toggle between invincible/mortal modes etc etc.
Trojans:
Nasty virus like attachments which can be merged with executable files. These are tiny so are unlikely to arouse suspicion. When run they allow a hacker to access your computer and wreak havoc. Can occasionally be found in warez files.
UBB:
Shorthand for Ultimate Bulletin Board, currently the most popular script used for creating warez bulletin boards.
UBB Hacks:
This term falsely gives the impression that something destructive or malicious is involved, but when you hear people talking about a hack in the context of bulletin boards they are simply referring to code which helps to improve the functionality of a board. For example a "thread hack" would effect the way in which individual threads look and operate.
Undeletable Pub:
An anonymous access, public FTP site where the permission attributes are set to allow uploads and downloads, but do not permit deletion.
Unzip:
Unpacking or decompressing many files that have been stored in a single archive. Technically only used when talking about zip files.
Upload:
Copying files from your computer to a web server or FTP site using a modem.
URL:
Stands for "Uniform Resource Locator". The web site address you type into your browser.
Voting:
Members of the warez scene are very keen to reach the number one slot of top lists such as Voodoo, Top 60 etc. and will therefore encourage you to vote for their site to improve their position and get the credit they deserve (or not as the case may be!).
Warez:
Full version software that is uploaded to the internet and is available for free download.
Warez Board:
Bulletin board used by the warez community to share links and discuss anything related to warez.
Winace:
Another utility used for decompressing all the common archive formats. Not great in my opinion. See below for a better one.
Winrar:
Utility used for decompressing .rar files and much more.
Winzip:
An essential tool used to decompress warez files.
Zip:
A common compression format used to store warez .
Subscribe to:
Posts (Atom)



